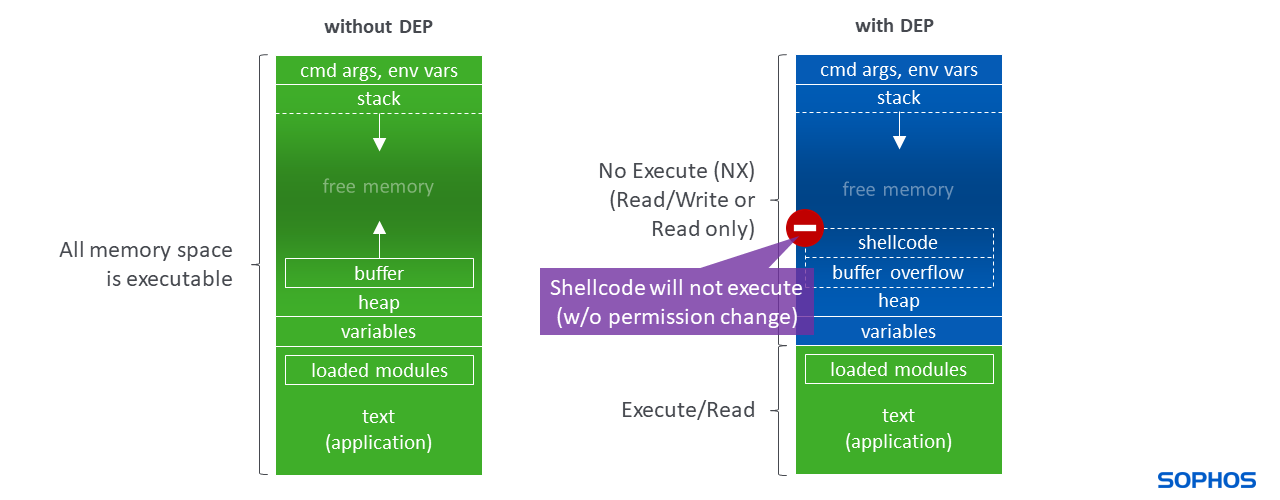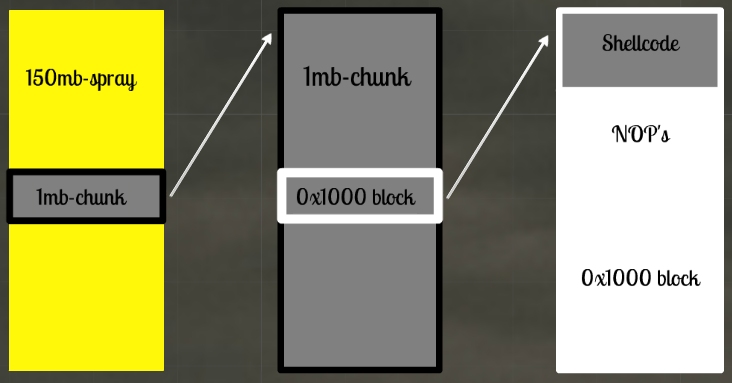
Heap Spray Exploit Tutorial: Internet Explorer Use After Free Aurora Vulnerability · The Grey Corner

PPT - Nozzle: A Defense Against Heap-spraying Code Injection Attacks PowerPoint Presentation - ID:2510980

Reverse Engineering and More on Twitter: "RE tip of the day: In heap spray, attackers use nop sleds/ramps that involve filling in allocated memory with a byte 0x90 encoding the NOP instruction
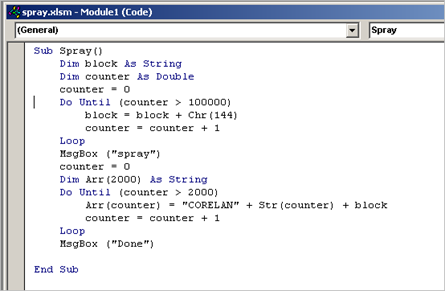
Exploit writing tutorial part 11 : Heap Spraying Demystified | Corelan Cybersecurity ResearchCorelan Cybersecurity Research

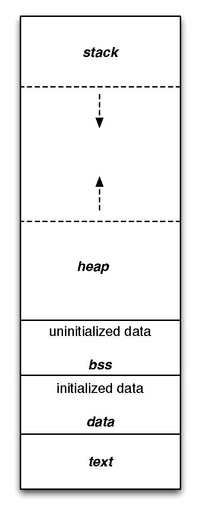
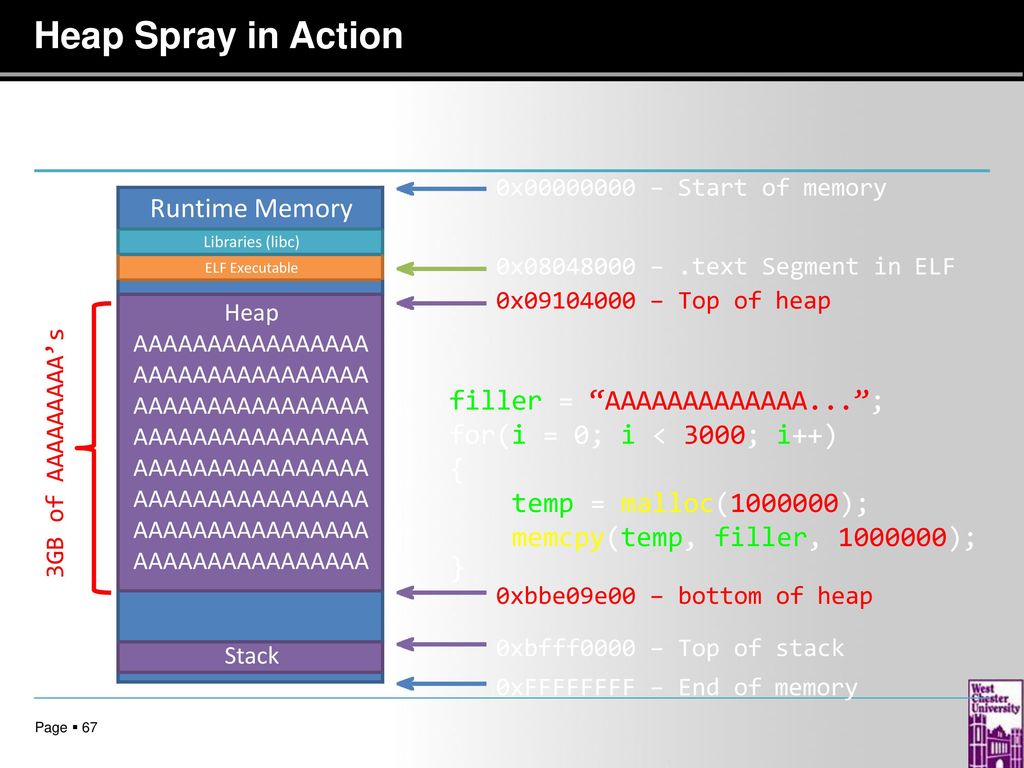
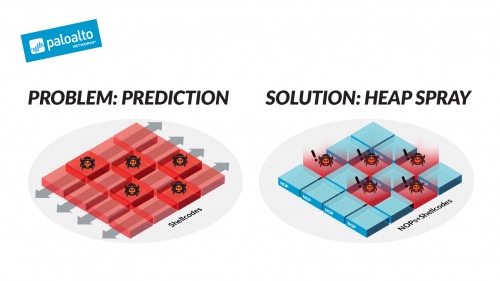

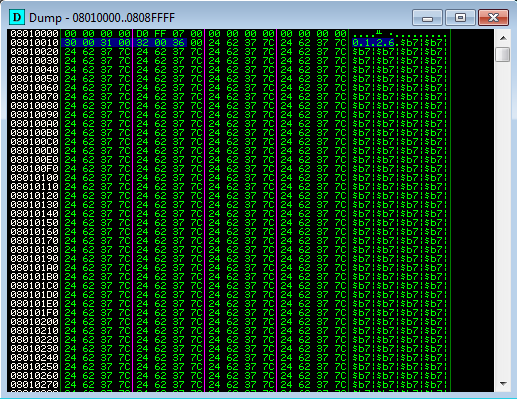






![PDF] NOZZLE: A Defense Against Heap-spraying Code Injection Attacks | Semantic Scholar PDF] NOZZLE: A Defense Against Heap-spraying Code Injection Attacks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/24b2f987c6a1b633df3a8ca970ce59a7259fd482/4-Figure3-1.png)